Censys

The Authority for Internet Intelligence and Insights

Censys Internet Map
Security teams not only need real-time visibility, but insights they can act on. Censys provides modern security teams the Internet intelligence they need to stay ahead.
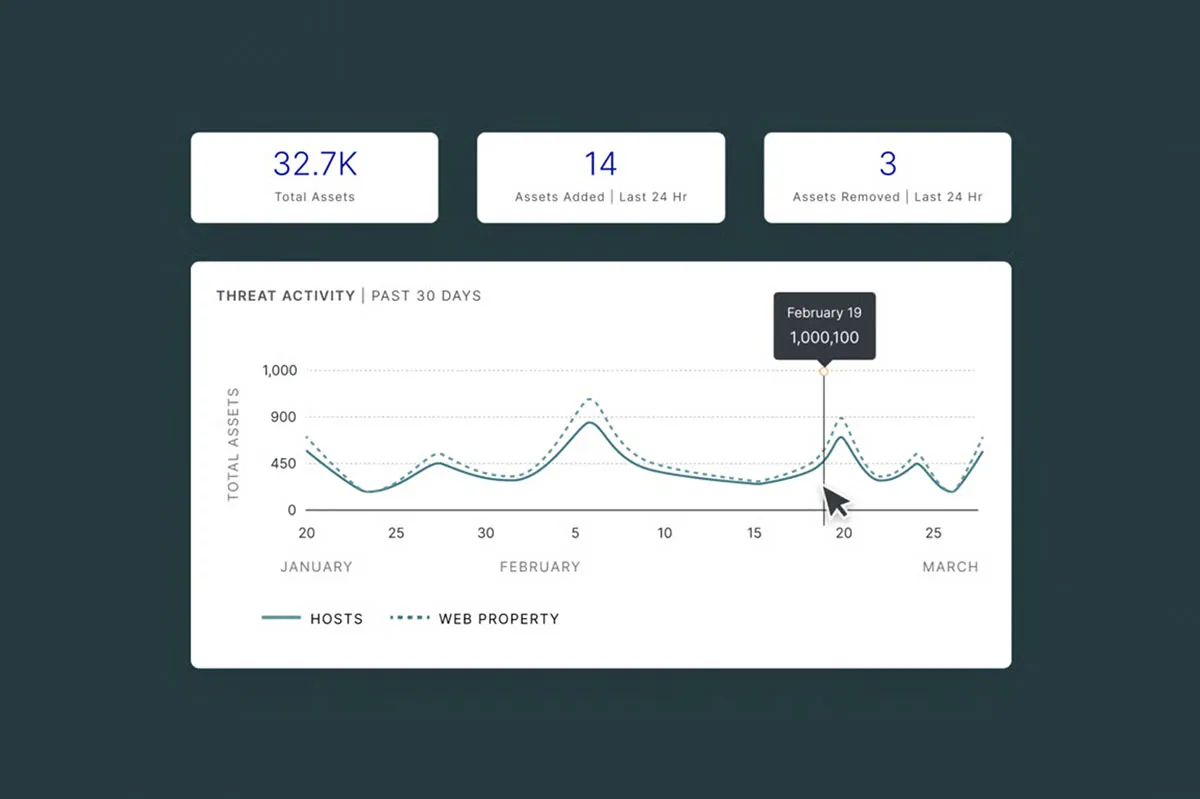
The best insights come from the best data. Censys’ foundation is our industry-leading Internet Map that provides real-time data about all Internet infrastructure. Our unmatched visibility enables us to uncover the most important insights for security organizations in real time.
You can explore, analyze, and drive decisions using the Censys Platform — a comprehensive tool for understanding your exposure, your dependencies and blind spots, other Internet players, and attackers’ infrastructure.
Intelligence and Insights
Attack Surface Management, Threat Hunting, and Proactive Cyber Defense
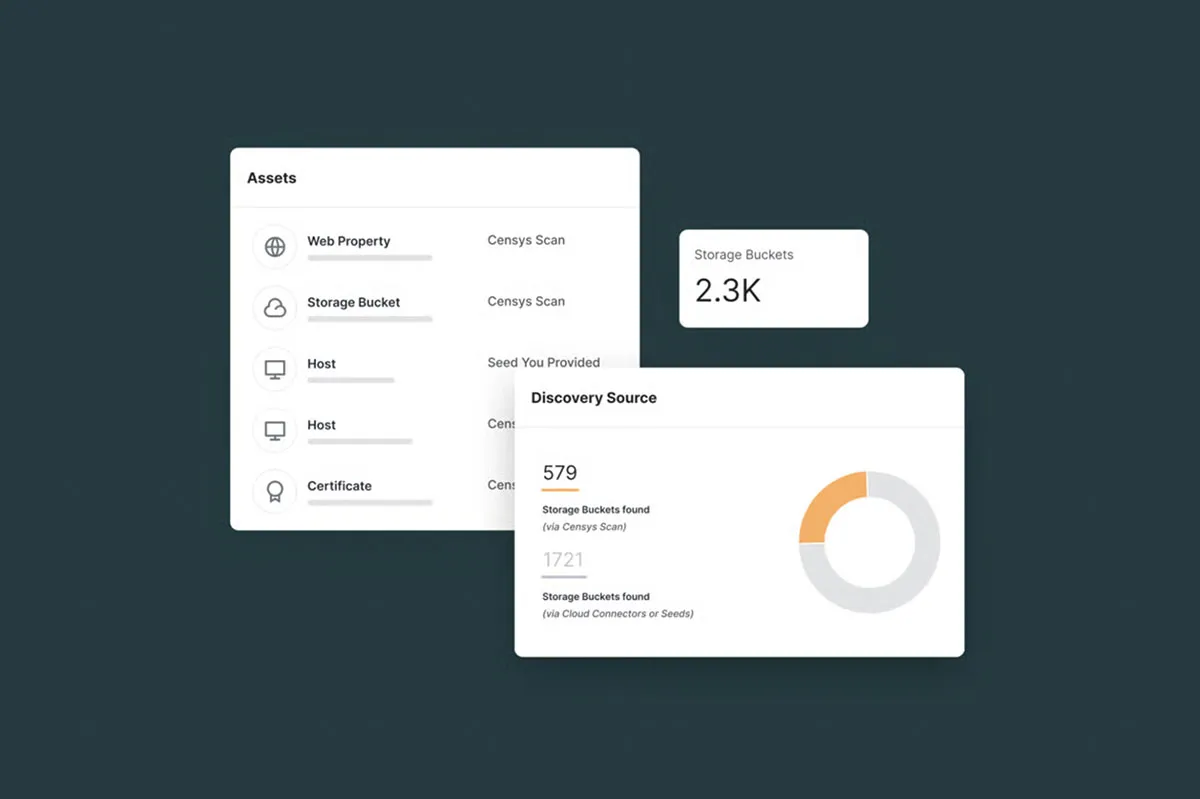
With the Industry’s best Internet intelligence at your fingertips, it is easier than ever to accomplish your security objectives at scale — whether it be discovering your digital footprint, identifying unknown exposures, or tracking attacker infrastructure.
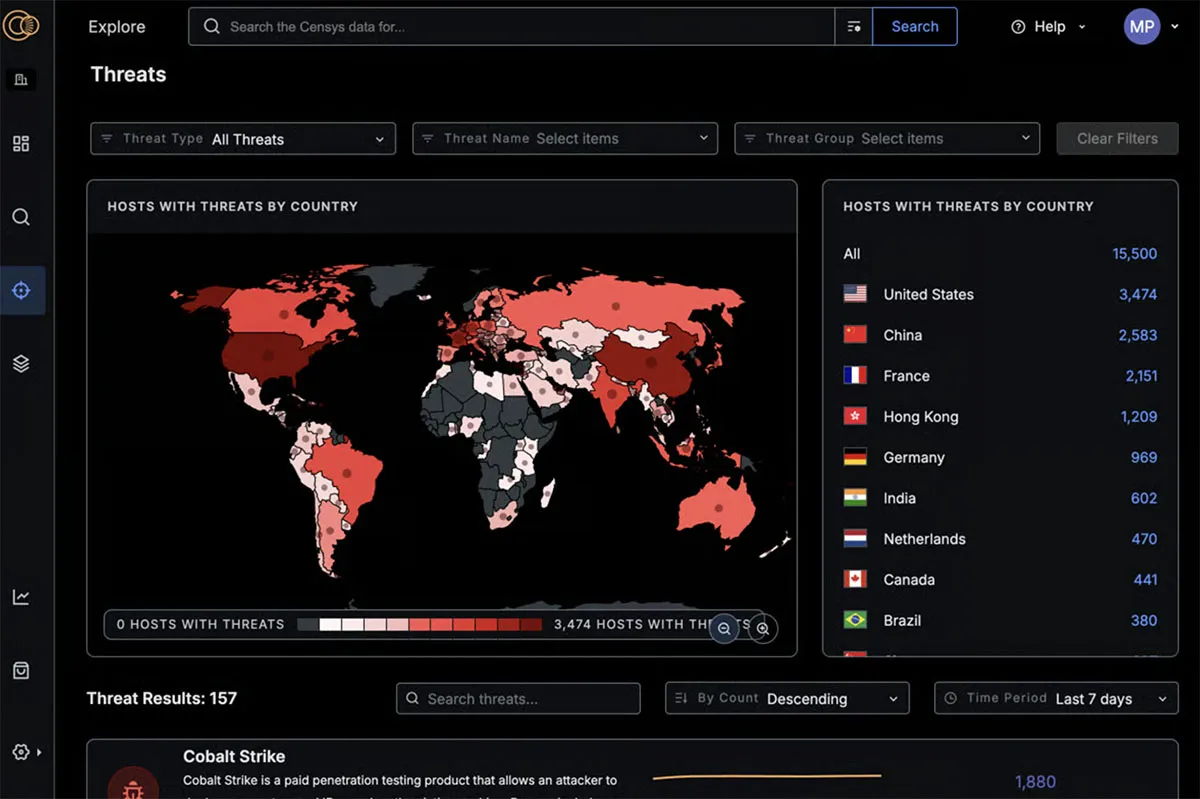
Stay ahead of an evolving threat landscape with access to the rich, contextualized intelligence on the infrastructure that threat actors are using to mount attacks. Use our highly-structured Internet data to detect compromises, uncover attacker-controlled infrastructure, and identify new attack methods.
Understand and remediate the Internet exposure of the control systems and power national critical infrastructure. Gain real-time visibility into your, ICS environments, mitigate threats of disruption, and protect operational resilience.
Gain complete visibility into the cybersecurity posture of subsidiaries and potential acquisitions. Quickly uncover hidden cyber risks with real-time insights, empowering your security team to make informed decisions about infrastructure they might not otherwise have visibility into.
Censys provides security analysts with the Internet visibility and context they need to quickly uncover and respond to incidents, to identify anomalous events, and to prioritize remediation efforts. Access a comprehensive, continuously updated view of global Internet infrastructure to get a clear picture of your own Internet presence, your suppliers, and your adversaries.