Picus

Security Validation Platform
Quantify risk and consistently discover, validate and mitigate with real-world simulations.
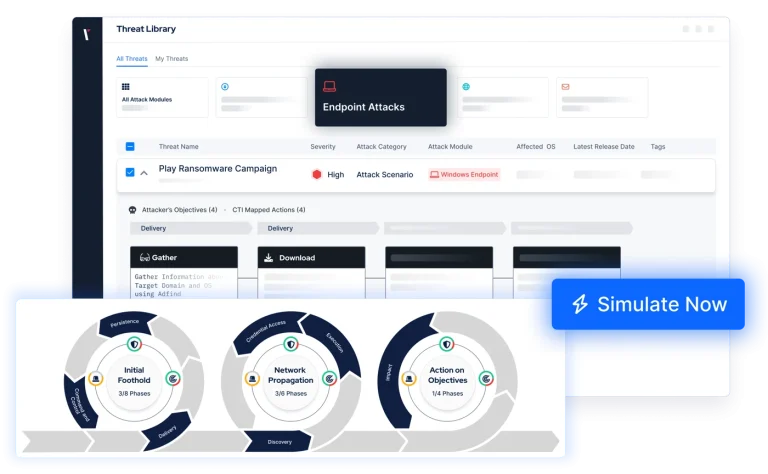
Security Validation Powered by Breach & Attack Simulation
Overcome the challenges of manual security assessments by consistently validating your security against the latest real-world threats with our security validation platform.
Simulate tactics and techniques across the cyber kill chain and address gaps swiftly and effectively with a cutting-edge BAS solution—no offensive security expertise required.
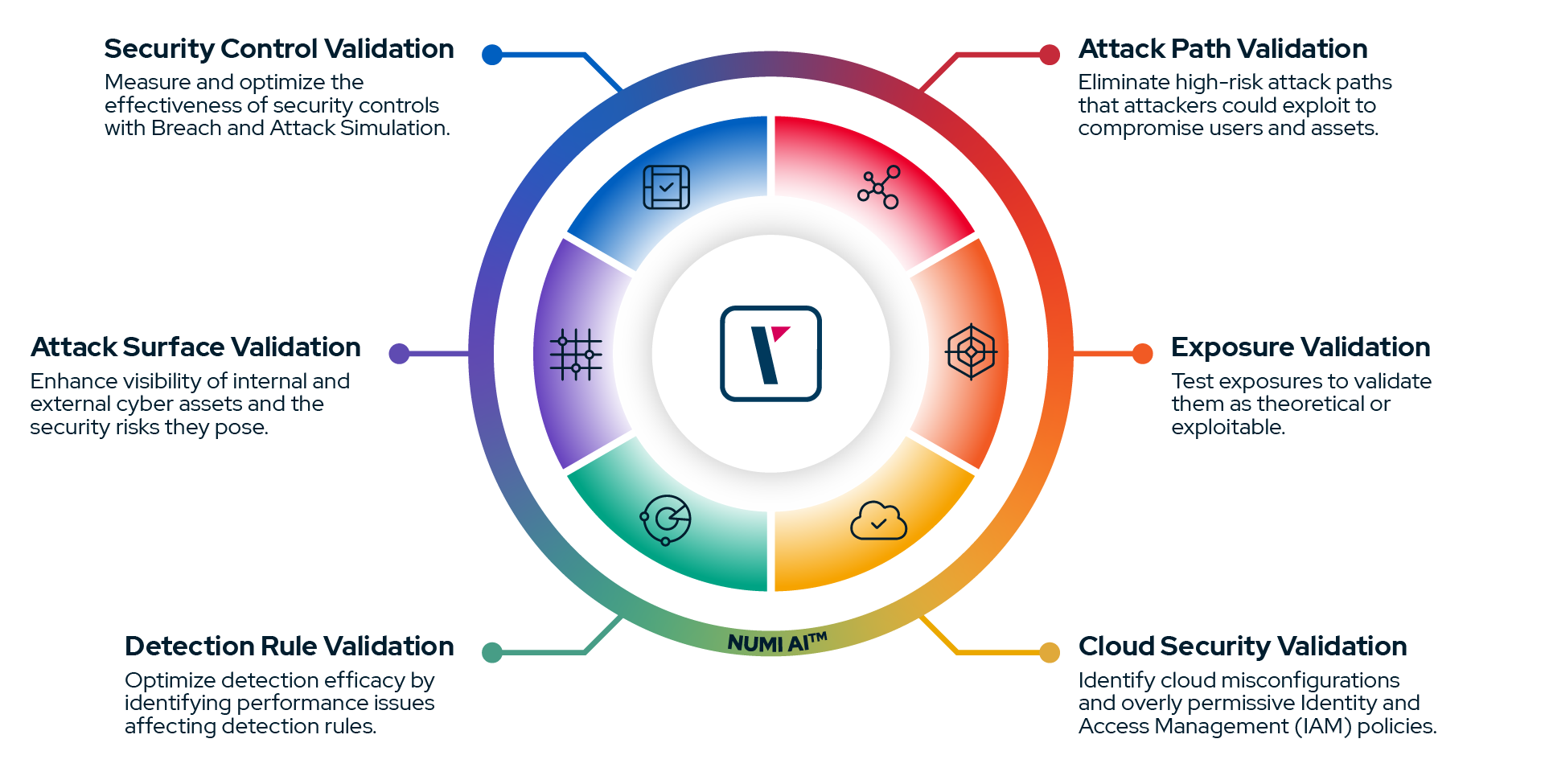
Benefits of Security Validation
Validate your security inside out and outside in.
Save time by automating validation workflows.
Simulate attacks on-premises and in the cloud.
Insights for red teams and blue teams.
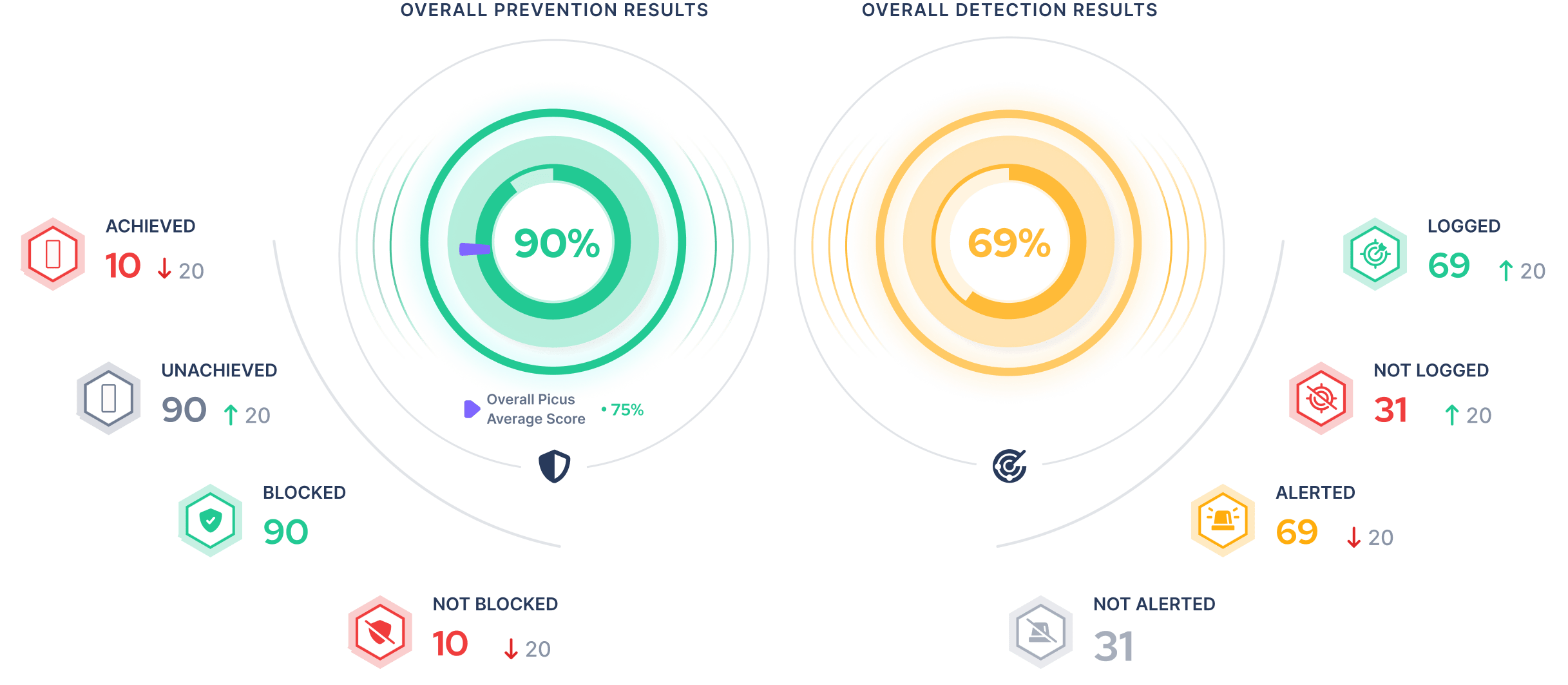
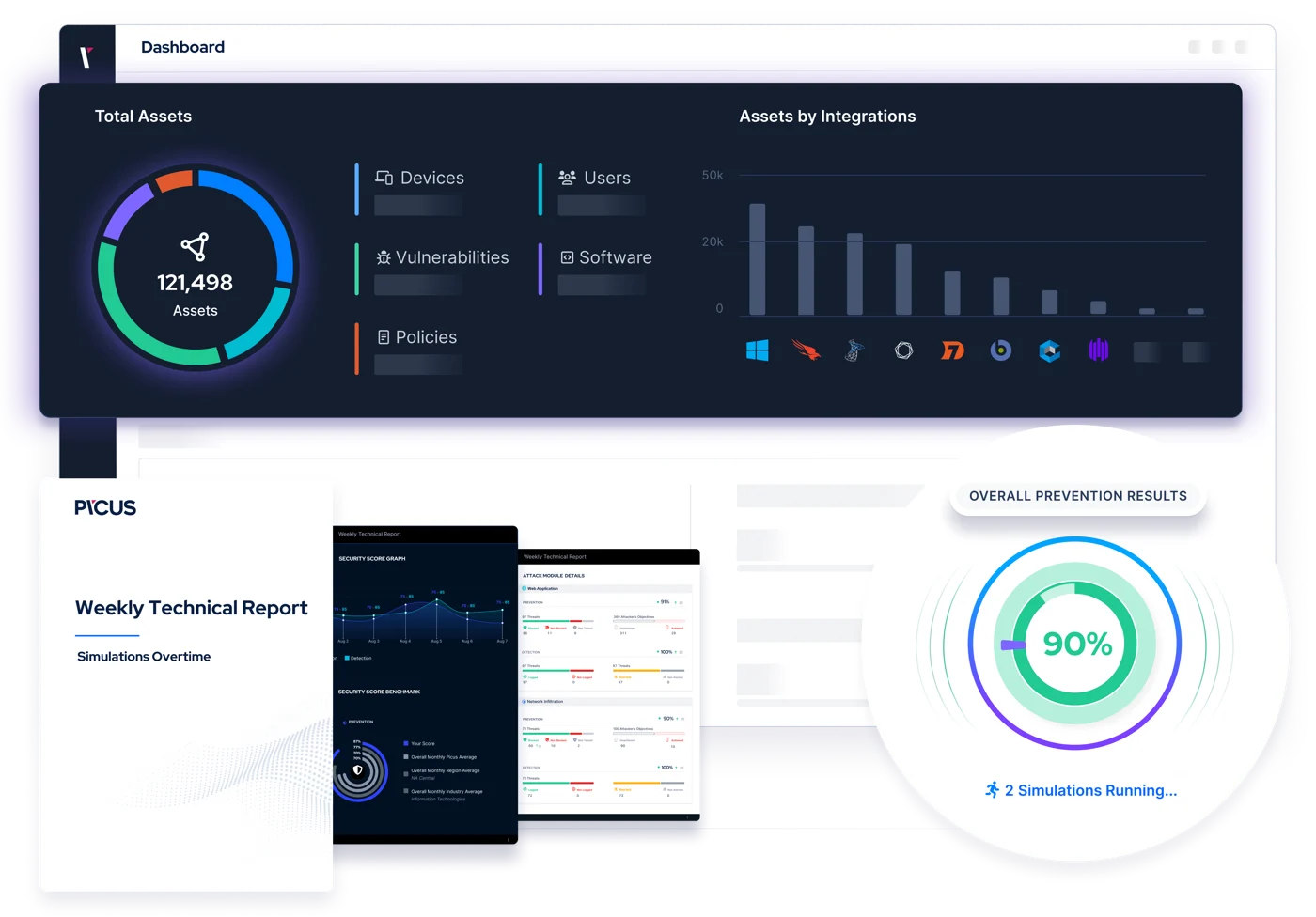
Quantify Your Cyber Risk
Get the insights you need to measure effectiveness, make critical decisions, and prove your security posture with automated security validation.
- Consistently assess your prevention and detection controls.
- Track security improvements in real-time.
- Share evidence with stakeholders.
Reduce Threat Exposure
Get the visibility and context to focus on what matters most.
- Get broad and up-to-date visibility of your internal and external assets.
- Validate based on the latest cyber threat intelligence and vulnerabilities using automated BAS.
- Make prioritized security decisions.
Maximize Impact with Actionable Insights
Identify security gaps, and address them swiftly and effectively.
- Quickly access mitigation suggestions to address policy gaps and misconfigurations.
- Use vendor-specific rules & signatures to optimize security controls.
- Get intelligent insights driven by AI.
Validate and Optimize Effectively
Numi Al Virtual Security Assistant
Got a question about your organization’s security posture? With Numi Al, the Picus platform’s virtual security analyst, obtain the insights you need to quickly gauge its threat readiness and make risk-based decisions.
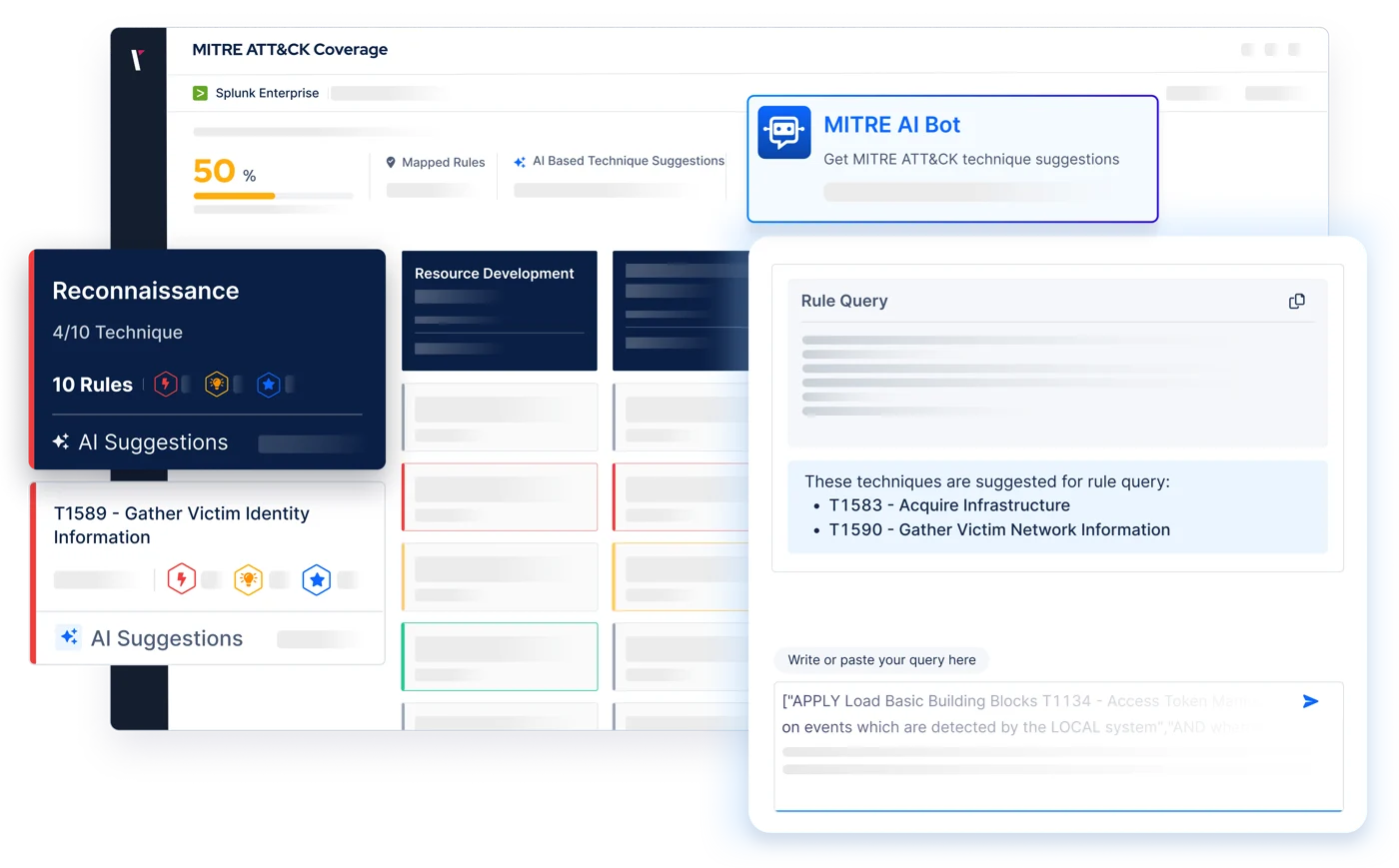
MITRE ATT&CK Mapping
Visualize the threat coverage provided by your security controls against MITRE ATT&CK. See the coverage provided by your SIEM and EDR rules and optimize based on the results of attack
simulations.
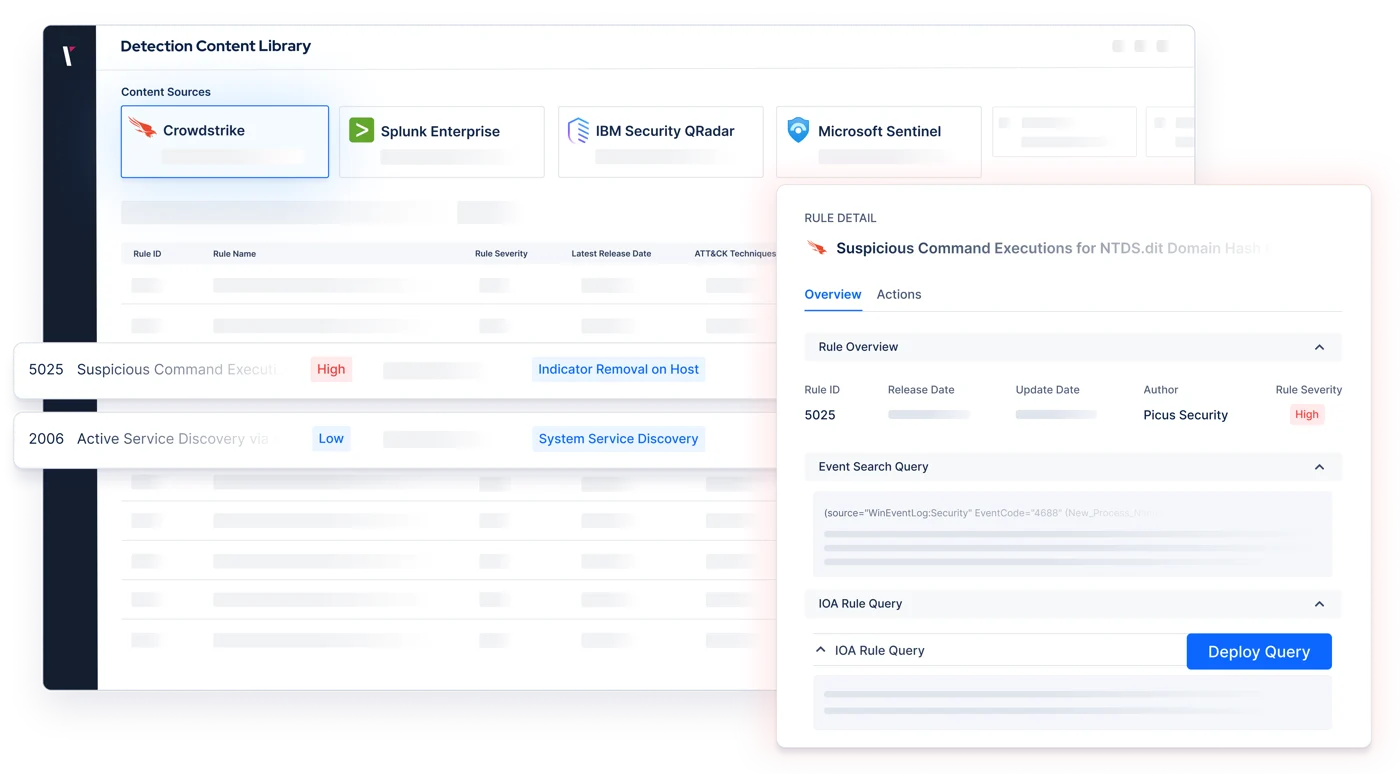
Mitigation Recommendations
Alleviate the strain of security engineering. Quickly address policy gaps with vendor-specific and generic signatures and detection rules for prevention and detection controls.