OneIM Identity Governance And Administration (IGA)
Complete, business-driven governance for identity, data and privileged permissions
See how you can implement enhanced identity governance and administration capabilities to better manage all users for your on-prem, hybrid and cloud environments. Satisfy audit and compliance initiatives, and easily provide management with a clear view of your governance posture. Meet attestation and recertification requirements with ease. Quickly access data about internal, external and privileged accounts that have access to your on-premises, cloud and hybrid applications to easily pass audits.
Ensure that access for all users and to all systems is accurate and appropriate – and all identity decisions and actions follow policies and can be reported on.
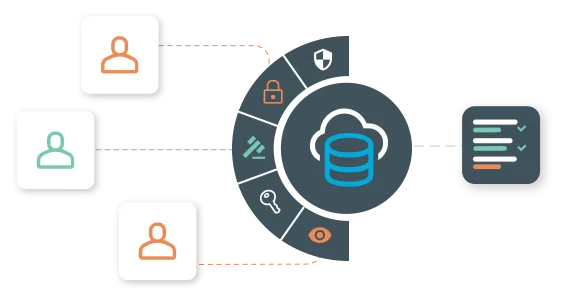
Identity lifecycle
Grant access rights by defined roles, rules and policies. Deliver standard on-boarding and off-boarding processes for employees and contractors, and quickly and easily manage access to resources as a user’s responsibilities evolve along with the business. The how identity governance and administration solutions are meant to work.
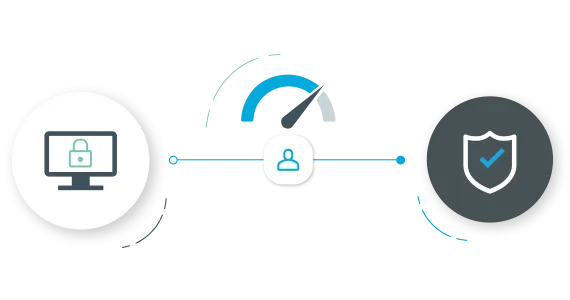
Access certification
Streamline identity governance and administration processes, including managing user identities, controlling privileges and configuring security across the enterprise. These capabilities extend to user application access, unstructured data and privileged accounts. Achieve all this by placing user management and access control into the hands of authorized business users.
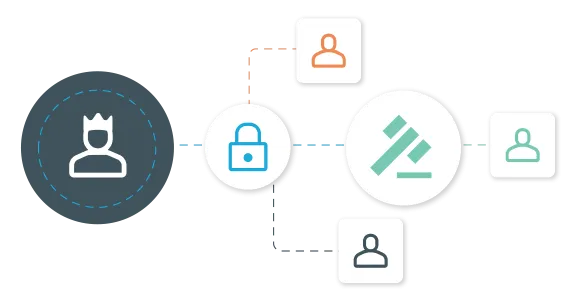
Privileged account governance
Extend governance to privileged accounts and administrator access with unified policies, automated and business-driven attestation, enterprise provisioning, and access request and fulfillment. Simplify privileged governance with defined roles and associated policies, access-approval workflows and perform periodic attestation of privileged access.
Access request
Enable users to request access to network resources, physical assets, groups and distribution lists and control access rights and permissions for their entire identity lifecycle while using predefined approval processes and workflows.
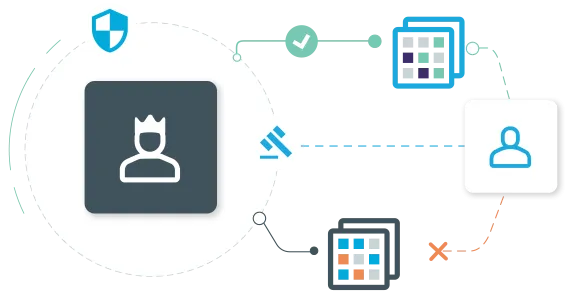
Auditing
Deliver audit-ready reports to meet ongoing compliance requirements. Provide auditors with detailed, real-time reports that includes identity governance and administraton data about what resources are in your environment, who has access to them, when, and why that access was granted and terminated.
Data governance
Extend the governance advantages of unified policy, automated and business-driven attestation, enterprise provisioning, and access request and fulfillment to privileged accounts and administrator access. Simplify privileged governance with the ability to define roles and associated policies, access approval workflows and perform periodic attestation of privileged access.
Identity governance for SaaS applications
Extend identity governance and administration advantages of unified policy, automated and business-driven attestation, enterprise provisioning, and access request and fulfillment to privileged accounts and administrator access to your SaaS applications.

